This is the second research note from Pallavi Paul, one of the short-term social media research fellows at The Sarai Programme.
In truth the subtle web of thought
Is like the weaver’s fabric wrought:
One treadle moves a thousand lines,
Swift darts the shuttle to and fro,
Unseen the threads together flow,
A thousand knots one stroke combines.
– Goethe, Faust
Emplotted within crucial challenges posed by the digital, the entry of electronically coded words, images, text and events in courts of law has been one of the most significant events of this century. The Information Technology Act (2000) defines electronic records as “data, recorded or generated , image or sound stored, received or sent in an electronic form or micro film or computer generated micro fiche” [1]. Further, Digital Forensics is the process by which these sources are investigated and reinterpreted as ‘evidence’. This project, by which a series of mathematical algorithms is given a decisive charge in the processes of law and justice, rests on a curious philosophical conundrum. The sources of electronic data can be wide ranging to include computers, cameras, network servers, music devices, DVDs, VCDs, computer hardware, routers, cell phones, websites, social media accounts, hard drives etcetera. What contributes to this ever burgeoning list is the agility of the digital form. Unlike the incompatibility of say, celluloid strips with gramophones, contemporary units of bit and bytes can inhabit a computer screen, an Ipod and a DVD with equal ease. In other words, technologically, the digital signal thrives on resemblance or a specific form of analogousness. The field of forensics on the other hand, is structured by the notion of ‘‘individualization’’. In his discussion on New Media and the Forensic Imagination, Mathew Kirschenbaum notes, “…the forensic principle of individualization insists upon the uniqueness of all physical objects. The core tenets of individualization construct a form of hard materiality.”[2] He goes on to note that in accordance with this no two things can ever occur, be constructed or even break in the exact same way . To understand the implications of this material logic for digitally encoded images we must turn to Kenneth Thibodeau’s tripartite model for defining digital objects [3]. Thibodeau notes that digital objects are constituted of the ‘physical’ dimension i.e. the device and form in which it exists for instance a magnetic tape or a camcorder. They also exist as ‘logical’ objects i.e. via the systems of code they deploy e g. software or the manner in which data files are organised and finally digital objects exist as conceptual objects i.e. in its encounter with the lived world and its implications on everyday life e g. As a photograph or a piece of music. By making the conceptual dimension an integral part of the digital object, Thibodeau is able to extricate the ‘information object’ from the appearance of digital homogeneity. Further, if we are to preserve a digital object it is important to retrieve all its physical, logical and conceptual dimensions [4]. The question of not only the hardware, software but also the conditions under which the data was produced and circulated becomes the very basis on which the digitality of an object can be established and verified. The role of digital forensics then becomes one of negotiating the ever compounding realms of the physical, logical and conceptual. The recovery of the digital interface of an event, can be thought of as recovering the uniqueness of its trace on hardware and software alike.
Responding to an interview conducted in his office, Mr. K C Varshney the deputy director and quality manager of the Forensic Science Lab, Rohini informed me that every month his lab receives around 10- 20 cases involving video. “Our main job is to see whether or not this video is authentic. We check for edits in sound and visuals. Sometimes we are also asked to enhance the quality of certain files, so that the investigating agency can get a better idea of the crime scene.” [5] Within the FSL, video forensics lies in the department of physical sciences. The long grey corridor of the building which leads one to the video lab is flanked on either sides by departments such as serology, ballistics, lie detection division, documents division, fingerprints division [6]. Mathew Kirschenbaum’s discussion on the materiality of digital material comes back with a palpable force as one senses the presence of video material amidst other materials like bones, blood, cement, glass, hair, metal, paper, plastic, cloth etectera . Mr. Sanjeev Gupta, the Assistant Director of the Cyber Cell explains the procedure through which video material reaches the forensic science laboratory. “Our primary client in these cases is the Delhi Police. The first step is that Delhi Police sends us a formal request to get involved with a brief description of the case. If found suitable for intervention, we ask for a list of exhibits with a description of each exhibit collected from the crime scene. Following this the exhibits, which may include video files, playback devices, computers etcetera are sent to us. Depending on the nature of the exhibits we then involve manufacturers or vendors of certain softwares or devices to get a better understanding of the exhibit .” [7] In their discussion on digital forensics Neha Kishore, Chetna Gupta and Dhvani Dawar delineate the rules of producing digital evidence in the court of law. While establishing authenticity of the primary material is a significant part of the forensic enterprise they observe that in addition to this the forensic expert must also establish the reliability of the computational method, the completeness of the evidence taken into account, the evidence must be shown as free from any ‘contamination’ during forensic handling and finally an ‘evidence custodian’ or a detailed journal describing with date and time the various interventions made by the forensic expert must be produced in court.[8]
Currently the production of video, audio and other electronic material as evidence in Indian courts falls under the ambit of the Indian Evidence Act of 1872 [9]. The Evidence Act makes an observation on two sites of the production of evidence – oral testimonies and documents. On oral evidence, the act observes that unless made during the proceedings of the court an oral statement would be inadmissible as evidence in any given case. Stated in principle 59 and 60 this is the hearsay rule of the evidence act. About documents, the act notes that in order to prove the contents of the document primary or secondary evidence must be offered. These include certified copies of the document produced by processes that ensure accuracy and/ or the testimony of people who have seen the document. This becomes especially significant in cases where the original document cannot be produced in court owing to damage, loss or possession by hostile parties. Before the introduction of the Information Technology Act (2000), Indian courts would regard the digital document as primary evidence and authenticated print outs and records generated for it as secondary evidence. In this manner the colonial evidence act had been simply adapted to the digital, without destabilizing the statutes of the hearsay rule [10] . This separation between the digital object and its material realization, however, proved to be unsustainable with the radical changes in technology and the enmeshment of data with networks, software with hardware and circulation with production. Under the Indian Evidence Act two new provisions 65 A and 65 B were introduced to deal with electronic evidence. While section 65 A distinguishes electronic evidence from oral and documentary evidence, ensuring special provisions for its authenticity, sanctity and retrieval; section 65 B details this special procedure. The certificate of authenticity produced in compliance of the section 65 A and 65 B must “uniquely identify the electronic record” [11] , describe the manner of its creation, describe the device that created it, and certify compliance with technological conditions for example checking the optimum functioning of devices such as computers, CD writers etcetera.
In the light of the preceding observations it is perhaps safe to say that at the heart of the forensic enterprise the question of the ‘authentic’. In his discussion on digitality, authenticity, decay and memory, Sean Rupka asks, “where does the authority of the digital object emanate from?” [12] he observes that the inherent fragility of the digital medium for example erasability, re-writability, generation loss, obsolescence of formats etcetera makes “ digital objects exist less as authoritative isolated objects and makes them more dependent on relationality and multiple, co-existent and even contradictory structures of memory .” [13] This idea of relationality as authenticity becomes interesting when we begin to think of authorized copies. A copy, one can say, is a form of memory that has been relocated from the original , onto another surface or object. Further, this relocation must be authenticated in order to assess the possible mutations from its source. The act of authentication of memory, however, is undertaken mostly in moments of crises. When to prove or disprove a memory becomes of utmost importance the ‘original’ usually finds itself challenged and even reconstituted. As a philosophical provocation one can go so far as saying that rather than being authenticated by the original, it is now the copy that authenticates the original. It does this not through a relationship of simple reproduction of the original but via its persistent trace in the path of the original. In doing this the authentic copy is now contending with it’s logical other, the rejected reproduction of a yet to be authenticated original. In her discussion on ‘e-jects’ i.e. rejected electronic objects/ information Dene Grigar notes
“When we erase a file, the file does not cease to exist, though sometimes we wish it would go away. The code that makes up the file persists somewhere in the machine that we just cannot easily get to. When we orphan a document with an upgrade to our system, that document does not disappear, though it may seem that we have lost it forever. Information on floppy disks, diskettes, and CDs we hold on to still remains the information on floppy disks, diskettes, and CDs. The fact that we cannot get to it says more about our need for better, faster, more robust than the e-ject’s durability. That e-jects can be recovered are not evidence of their durability but rather of their status as texts. They are “acts of communication” that lend themselves, as all texts, to “acts of translation.” Recreated, they are new.” [14]
These truant, phantom copies then seem to be challenging the original on its very own terrain. Distinguished until now from all its copies only by its immutability and persistence, the electronic original is now standing across its own alter ego. The rejected file which refuses to change.
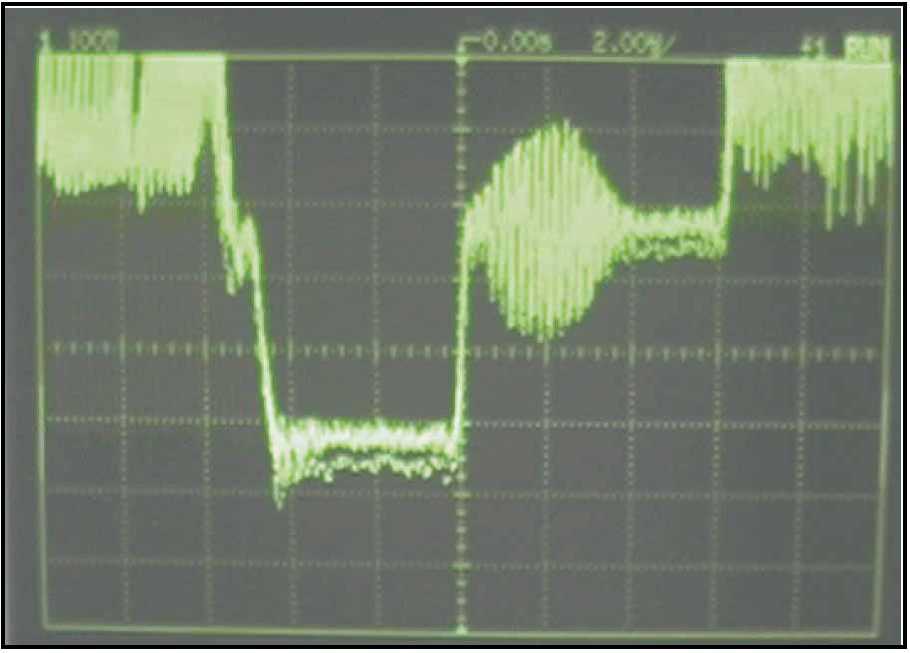
This relationship resonates in interesting ways in the case study undertaken by officer C.S. Singh in his 2006 article in the Indian Police Journal. Writing on the ways in which video evidence can be forensically decoded Singh notes that the main concern of the investigation is to determine whether “the videotape is a copy, a compilation of other tapes, or an edited version.”[15] Computing the degradation of the video signal according to Singh has emerged as a significant way of determining whether or not the video material in question is an original or a copy. It must be noted however, that the forensic examiner has to take into account that producing multiple copies is only one of the reasons that can cause the video signal to decline owing to generation loss . The other reasons for decline in signal strength include the characteristics of the camcorder and the playback device used to record and play the original tape. As a way of studying the disputed video recording, Singh describes an experiment that was undertaken by the Central Forensic Science Laboratory . The video camera which had been used to shoot this video was used to shoot twenty minutes of fresh video in both dim and brightly lit conditions. Five generation of copies were then produced from this original recording. Further the video copies were played back through the same system and a cathode ray oscilloscope ( model no: SM 1001 ) was used to compute the video voltage levels of the recordings. These levels were then imaged on a waveform monitor. The voltage of the video sample was then deduced using the same equipment and the results were juxtaposed to determine that the video voltage of exhibit matches which generation of video samples from the experiment.

Fig. Superimposition of Video Waveform of 1) the disputed recording and Original 2) the disputed recording with the copy of the camera original
It is interesting to note here that it is essential that multiple copies be produced of the original in order to authenticate both the original and its subsequent copies.
Another aspect of video forensics is the shooting and reconstruction of crime scenes. Hardly ever admissible in court, this aspect of video forensics is concerned not so much with the production of evidence in judicial proceedings, but with providing investigating officers with a better understanding of the how an event occurred. The visualization of possibilities is the primary purpose of this enterprise.
In his interview Mr. K C Varshney ( Deputy Director, FSL) briefly explained the process of videographing a crime scene. The two most important aspects of forensic video he noted are “scale and continuity” [16] . The first instruction to videographers is to place a scale around all possible exhibits for the lab technician to get an idea about the exact size of the objects. Further, all objects must be shot from the perspective of a single identifiable object or space in a scene. For instance, if shooting outdoors “a metro pillar or a tree could work as possible reference objects.” Each exhibit seized from the crime scene should have been recorded on video along with the reference number of its seizure memo. At the start of the recording, the investigating officer is required to provide a short introduction describing the lay out of the area, date, location, time of day, an approximation of the time elapsed since the occurrence of the crime and the start of investigation. For maintaining continuity, the white balance, colour temperature and exposure of the frame is required to be constant. Further, every time there is a change in location a wide angle establishing shot must be taken to mark the transition. For small exhibits an extreme close up may be taken, preceded and followed by a contextualizing shot.
In their work on reconstruction of crime scenes using forensic animation, authors S. Lalwani, A. Raina, R.C. Pokle and T.D. Dogra note that while forensic video captures the scene as it was found, forensic animation is a technique of representing a “possible pattern” of a scene or incident. They lay out two forms of this practice. “Substantive Forensic Animations”, which animate known facts about a scene and “Demonstrative Forensic Animations” that illustrate possible occurrences or sequence of events [17]. The authors go on to present the following case study-
A forty two year old was driving to his daily walk when he suffered firearm injuries on various parts of his body. Crime scene reports suggested that the victim had been fired at from the front right window of his car, while he was in the driver’s seat. One bullet entry wound was present on his neck, three on the right side of his chest and one on the back of his right hand. However examination had also revealed that there was one bullet that entered the victim from his scrotum , went upwards through the abdomen and was recovered from the rear thoracic region. This one bullet made no sense vis a vis the description of the crime scene. The defense counsel raised this doubt using the expert testimony of the forensic expert that it was unlikely that a bullet could enter the victim’s scrotal region unless it was fired from the front of the vehicle. The examination of the vehicle, however, revealed that the front of the car had not been fired upon at all.
In this case the animated reconstruction of the trajectory of the bullets was done on the basis of anatomical position of the injuries and the testimony of eye witnesses present at the scene.
Constructed in the manner of a storyboard, forensic animation of the scene seems latent with possibilities of movement . Capturing something which could not be realized on video, the animated crime scene works to fill the gaps in visualizing various sequences of events. The authors go on to list possible situations in which forensic animation can be the only way to decode the scene- accidental fires and smoke spread patterns, air crashes, trajectories of bullets and bomb explosions. When seen through the phantom lens of the forensic camera, not only do these events begin to reconstitute themselves, but they also call upon the witnesses of the scene to review what happened before their eyes. Often constructed through the testimonies of those who have seen the event from different angles, the forensic animator is able to stack together multiple tangential fields of vision into which parts of the crime scene have leaked in. These are then transformed to create a deliberating forensic gaze that has the power to slow down bullets, structure smoke and erase fire.
Soon after FSL, Delhi (2009) was founded, Home Minister P. Chidambaram declared 2010 as ‘the year of forensics’ while inaugurating the XX Forensic Science Conference in Jaipur . He announced a ‘rapid modernization plan’ which included the opening of new laboratories, new criminal tracking networks, DNA databanks and proposed changes in the Arms Act [18]. In accordance with these initiatives two senior consultants Dr. Gopal Misra and Dr. C Damodaran from the Madras Forensic Lab were asked to collate and a present a report on the status of forensic science in India, alongside presenting possible directions for the future [19]. This report details the history of forensic science in India. Started by the British, the first forensic lab in India, The Chemical Examiner’s Laboratory was founded in 1849 in Madras. This was followed by Anthropometric Bureau (1892), Finger Print Bureau (1897), Inspectorate of Explosives (1898), Office of Government Handwriting Expert (1904), Serology Department (1910), Foot Print Section (1915), Note Forgery Section (1917), Ballistics Laboratory (1930) and Scientific Section (1936) Having subsequently undergone regrouping and expansion , there are now, 28 State / Union Territory Forensic Science Laboratories (State / UT FSLs) along with their Regional FSLs (32 RFSLS) and Mobile FSLs (144 MFSLs); these mostly fall under the jurisdiction of the Home Department either directly or through police establishment. During 1957, the first Central Forensic Science Laboratory (CFSL) was established at Calcutta, followed by the ones at Chandigarh (1961; traceable to Lahore – origin of 1933) and Hyderabad (1965). In 1971, Neutron Activation Analysis (NAA) Unit came into operation at Bhabha Atomic Research Centre (BARC), Mumbai. Thus the Bureau of Police Research & Development (BPR & D) administered three CFSLs, including NAA, and three laboratories of Government Examiners of Questioned Documents (GEQD). Presently (since 2002 / 03) they are all under the Directorate of Forensic Science (DFS; MHA, GoI); CFSL, Hyderabad has in its fold the NAA Unit and GEQD [20]. The report also proposed the introduction of The Forensic Act with the purpose of set ting up a body called the Forensic Council of India. It was proposed that this council would regulate the practice of various disciplines of forensics and lay down standards for accreditation and training. It was also proposed that an amendment be made to the Information and Technology Act Section 79 (A) which states that the experts from Forensic Science Laboratories would be called upon as expert witnesses in cases involving electronic evidence. The amendment expands the purview of the expert by suggesting that “The Central Government may also, for the purposes of providing expert opinion on electronic form evidence before any court or other authority, specify, by notification in the Official Gazette, any other Department, body or agency of the Central Government or a State Government or a Union Territory Government as an Examiner of Electronic Evidence.”[21] The report made a strong case for the introduction of audio and video training amongst forensic professionals. In recommendation number 18 to the Directorate of Forensic Science, Damodaran and Misra state the need for each CFSL to be linked via video conferencing. They also recommend that forensic professionals be kept abreast with latest audio and video recording gadgets and technologies. The lack of video research and training facilities are also highlighted in the equipment inventories of different forensic labs, presented in the report.
While 2010 was marked by government initiatives to create breakthroughs in forensic technology, this was also the year in which the mercy petition of Afsal Guru was turned down by the Delhi Government [22]. Accused in the parliament attacks case, Afsal Guru was deemed a suspect in police investigations through a series of phone records and wire tapped phone conversations. Even after repeated requests by the defense counsel to get the authenticity of these electronic exhibits forensically checked in accordance to the provisions of section 65 B of the Indian Evidence Act , the court not only admitted these electronic records but also made them a strong endorsement of Guru’s conviction. The Division Bench of Justice P. Venkatarama Reddi and Justice P. P. Naolekar observed:
According to Section 63, secondary evidence means and includes, among other things, “copies made from the original by mechanical processes which in themselves ensure the accuracy of the copy, and copies compared with such copies”. Section 65 enables secondary evidence of the contents of a document to be adduced if the original is of such a nature as not to be easily movable. It is not in dispute that the information contained in the call records is stored in huge servers which cannot be easily moved and produced in the court. That is what the High Court has also observed at para 276. Hence, printouts taken from the computers/servers by mechanical process and certified by a responsible official of the service-providing company can be led into evidence through a witness who can identify the signatures of the certifying officer or otherwise speak to the facts based on his personal knowledge. [23]
In addition to taking a technologically unsound view of electronic files, mechanisms of data transfer and retrieval, the bench also placed the onus of verifying signatures on employees of phone companies! Since this judgment there have been several cases in which claims and counter claims over the use of audio and video material in court proceedings have been made and contested. Some examples include the 2011 case of Amar Singh v. Union of India (2011) 7 SCC 69 [24] saw all the parties, including the state and the telephone company, dispute the authenticity of the printed transcripts of the CDRs, as well as the authorization itself. More recently, in the case of Ratan Tata v. Union of India Writ Petition (Civil) 398 of 2010, a compact disc (CD) containing intercepted telephone calls was introduced in the Supreme Court without following any of the procedure contained in the Evidence Act [25]. However, on 18th September 2014, the Supreme Court of India in the case Anvar v. P. K. Basheer (Civil Appeal 4226 of 2012) [26] took a new look at the evidentiary admissibility of the contents of electronic records. Justice Kurian Joseph, speaking for a bench that included Chief Justice Rajendra M. Lodha and Justice Rohinton F. Nariman, overruled an earlier Supreme Court judgment in the 1995 case of State (NCT of Delhi) v. Navjot Sandhu alias Afsan Guru(2005) 11 SCC 600, popularly known as the Parliament Attack case, and re-interpreted the application of sections 63, 65, and 65B of the Indian Evidence Act, 1872 (“Evidence Act”)[27]. The Supreme Court held that section 65 A and 65 B create special provisions that must be fulfilled in addition to the general law on documentary evidence. This not only meant that all the conditions for verification of electronic evidence must be met, which includes the production of an authentication certificate by a forensic expert; but also that oral evidence can no longer be called upon to attest electronic evidence. In it’s final judgment the bench noted that , “there has been a revolution in the way evidence is produced in court” .
An understanding of the forensic enterprise then, means an attempt to understand the force field that these simultaneously fragile and resilient, accelerated and inertial, domiciled and orphaned materials are exerting on our contemporary.
Notes
[1] The Information and Technology Act 2000. (2000). [online] Available at: http://www.dot.gov.in/sites/default/files/itbill2000_0.pdf [Accessed 23 Jun. 2015].
[2] Kirschenbaum, M. (2008). Mechanisms. Cambridge, Mass.: MIT Press. Pp. 63
[3] Thibodeau, K. (2002). Overview of Technological Approaches to Digital Preservation and Challenges in Coming Years1 — Council on Library and Information Resources. [online] Clir.org. Available at: http://www.clir.org/pubs/reports/pub107/thibodeau.html [Accessed 23 Jun. 2015].
[4] Kirschenbaum discusses Thibodeau’s argument in the introduction of Mechanisms (2008)
Kirschenbaum, M. (2008). Mechanisms. Cambridge, Mass.: MIT Press pp. 3
[5] Varshney, K. (2015). On Forensic Practice Today
[6] Kirschenbaum, M. (2008). Mechanisms. Cambridge, Mass.: MIT Press.
[7] Gupta, S. (2015). Video Forensics Procedures.
[8] Kishore, N., Gupta, C. and Dawar, D. (2014). An Insight View of Digital Forensics. International Journal on Computational Science & Applications, 4(6), pp.89-96.
[9] The Indian Evidence Act, 1872. The Indian Evidence Act, 1872. [online] Available at: http://chddistrictcourts.gov.in/THE%20INDIAN%20EVIDENCE%20ACT.pdf [Accessed 23 Jun. 2015].
[10] Anvar v. Basheer and the New (Old) Law of Electronic Evidence. (2014). [online] Available at: http://cis-india.org/internet-governance/blog/anvar-v-basheer-new-old-law-of-electronic-evidence [Accessed 23 Jun. 2015].
[11] Symantec.com, (2014). Indian Evidence ACT Section 65A and Section 65B. [online] Available at: http://www.symantec.com/connect/blogs/indian-evidence-act-section-65a-and-section-65b [Accessed 23 Jun. 2015].
[12] Rupka, S. (2014). Digitality, Authenticity, Decay, Memory. [Blog] -empyre- soft_skinned_space. Available at: http://empyre.library.cornell.edu/phpBB2/viewtopic.php?t=639&sid=e86cf7d86ab55fc55bee33fa51007331 [Accessed 23 Jun. 2015].
[13] ibid
[14] Grigar, D., Tabbi, J., Tata, M., Heckman, D., Kirschenbaum, M., Angel, M. and Gibbs, A. (2009). E- ject: On the Ephemeral Nature, Mechanisms and Implications of Electronic Objects. 1st ed. [pdf] Irvine: University of California, pp.1-7. Available at: https://escholarship.org/uc/item/2xv6b6n0 [Accessed 24 Jun. 2015].
[15] Bureau of Police Research and Development, Ministry of Home Affairs, (2006). The Indian Police Journal Vol. LIII No. 2, April-June 2006. New Delhi: Ministry of Home Affairs, pp.78-82.
[16] Varshney, K. (2015). On Forensic Practice Today
[17] Lalwani, S., Raina, A., Pokle, R. and Dogra, T. (2014). Reconstruction of Scene by Forensic Animation: Two Case Reports. Journal of the Indian Academy of Forensic Medicine, Vol 36(No.1), pp.104-108.
[18] Correspondent, S. (2009). Chidambaram asks police to go in for new technology. The Hindu. [online] Available at: http://www.thehindu.com/todays-paper/tp-national/chidambaram-asks-police-to-go-in-for-new-technology/article140909.ece [Accessed 24 Jun. 2015]
[19] Mishra, D. and Damodaran, D. (2010). Perspective Plan for Indian Forensics. New Delhi: Ministry of Home Affairs, pp.1-511.
[20] ibid, pp 23-25
[21] ibid, pp 458-59
[22] Today, Headlines . (2010). Centre Rejects Afsal Guru’s Mercy Plea. India Today. [online] Available at: http://indiatoday.intoday.in/story/centre-rejects-afzal-gurus-mercy-plea/1/102675.html [Accessed 24 Jun. 2015].
[23] The Centre for Internet & Society, (2014). Anvar v. Basheer and the New (Old) Law of Electronic Evidence. [online] Available at: http://cis-india.org/internet-governance/blog/anvar-v-basheer-new-old-law-of-electronic-evidence [Accessed 24 Jun. 2015].
[24] In the case Amar Singh former leader of the Samajwadi Party had approached the court against the Government of India and the Governmnet of Delhi alleging that on behest on the Indian National Congress his phone was being wiretapped and conversations recorded. Indiankanoon.org, (2011). Amar Singh vs Union Of India & Ors on 11 May, 2011. [online] Available at: http://indiankanoon.org/doc/1082001/ [Accessed 24 Jun. 2015].
[25] In the case industrialist Ratan Tata approached the Supreme Court accusing the Union of India of wiretapping his phone conversations thereby breaching his right to privacy. In a bid to protect his leaked conversations with lobbyist Nira Radia ,Tata cited a 2003 verdict of the European Court of Human Rights that held the government of Italy responsible for leaking the private conversations of Ex- Prime Minister Craxi. Courtnic.nic.in, (2014). Ratan N. Tata versus Union of India. [online] Available at: http://courtnic.nic.in/supremecourt/temp/wc%2039810p.txt [Accessed 24 Jun. 2015].
[26] This case involves the use of corrupt election practices. The appellant accused the respondent of delivering speeches, using propaganda songs and other visual material to defame him. The court refused to admit the electronic material produced in the proceedings on account of not being forensically verifiable.
Judis.nic.in, (2014). Anvar P.V versus P.K Basheer and Others. [online] Available at: http://judis.nic.in/supremecourt/imgs1.aspx?filename=41931 [Accessed 24 Jun. 2015].
[27] In the case Afsal Guru an employee of a pharmaceutical company was labeled an accused in the attack on the Indian Parliament in 2001.
Indiankanoon.org, (2005). State (N.C.T. Of Delhi) vs Navjot Sandhu@ Afsan Guru on 4 August, 2005. [online] Available at: http://indiankanoon.org/doc/1769219/ [Accessed 24 Jun. 2015].